Every year the unsuspecting public loses millions of its hard-earned dollars to phishing. The FBI estimates that phishing cost Americans nearly $30 million in 2017 alone. By taking a few simple steps to protect yourself, however, you’ll be less likely to become a victim of this scam.
Synchrony Bank will never ask for personal information by email. If you receive email from us offering links that is not from customer.service@mail.synchronybank.com, consumerbanking@e.synchronybank.com, consumerbanking@e.synchronybank.com, it may also be related to a phishing scam using our name. If you believe you’ve been targeted by a phishing scam using our name, call 1-866-226-5638.
What Is Phishing?
Phishing is using false communications in an attempt to trick someone into revealing personal or account information that can be used for identity theft. Although commonly seen as an email attempt, phishing isn’t confined to email. Scammers might use text messages, a technique known as “smishing,” or phone calls and voicemails, known as “vishing.”
- Deceptive phishing attempts often arrive in your email inbox as a message from what may appear to be a legitimate company—perhaps your own bank or a site you regularly use, or file-sharing services such as Dropbox or Google Docs. The email may ask you to visit the company’s website and enter your user name and password. In reality, the link takes you to a site run by cybercriminals in order to steal your login credentials. The links might also take you to a site that installs “malware” on your computer. This hidden software allows cyber attackers to collect your personal information.
- Spear phishing is a highly targeted form of phishing that includes personal details, such as your name or job title, in order to appear more legitimate. Spear phishing may have the same goal as deceptive phishing: to steal your personal information. But it can also be the first step in a more widespread attack on your employer or business, and it can happen on social media sites, including LinkedIn.
- Fraud happens after a phishing attempt succeeds. For example, cybercriminals may use your bank account login credentials to steal from your account. Or, if the attack is targeting a company, they might impersonate the owner, CEO or other top executive of a business, and send requests by email to the accounting department to wire money to their bank account.
- Pharming doesn’t bait people with fraudulent messages, but it’s still used to steal personal information and commit fraud. Attackers hack the websites of legitimate businesses and redirect visitors to another site that they control. Unfortunately, this means you can fall victim to a pharming attack even if you’re never contacted directly by a scammer.
How Common Is Phishing?
The FBI ranks phishing as the third most-common type of cyber attack. Every month, the Anti-Phishing Working Group receives more than 80,000 consumer reports of unique phishing campaigns—and each of those campaigns targeted multiple people. On the business side, 76% of organizations reported experiencing a phishing attack, according to a survey by Wombat Security.
How Can I Protect Myself from Phishing?
- Email essentials: First and foremost, be vigilant—even with links in email from sources that appear to be from a person or company you know or trust. Scammers are now sophisticated enough to send emails that look very much like they are from your friend, your bank or your favorite online store. Cybercriminals can even hack an acquaintance’s email account and use it to send you malicious links. Before you click on a link, hover over it, so you can see the URL where you’ll be sent. Don’t click if it doesn’t look legitimate. Be wary of attachments, poorly written email or any requests for your personal information. Banks and credit card companies generally have policies to never ask for this information by email. And remember, if the email seems to be designed to make you nervous or feel rushed, that’s suspicious.
- Be skeptical: Check the address and security of every website you visit. Be cautious when shopping online or anytime you’re entering personal information or a password. Check the site address carefully to be sure you’re exactly where you want to be. If, for example, you’re trying to log into “dropbox.com” but the URL reads “dropdox.com,” don’t enter your information. Most browsers today offer a symbol that you can use to easily check a site’s security: It’s a locked padlock icon next to the URL.
- Protect your information: To further reduce your chances of getting phished, avoid posting information on social networks that could be used for a spear phishing attack, use multi-factor authentication whenever possible and use a password-generation and management service.
- Educate your employees: If you own a business, train your employees to follow all these steps. Additionally, set up internal processes that prevent fraud. For example, you might require at least two people to approve all wire transfer requests.
I Think I’ve Been Phished. What Do I Do Now?
Nothing can completely prevent phishing, but if it happens to you, you have options. Start with these four steps.
After you take these initial steps, contact others to make sure your information isn’t being used by hackers. To isolate potential financial damage, contact Equifax, Experian or TransUnion, the three credit reporting agencies, and have a fraud alert placed on your account. Contact your bank and credit card company and follow their instructions. You may need to freeze or cancel your cards. Then continue to monitor your accounts frequently so you can catch any unauthorized transactions.
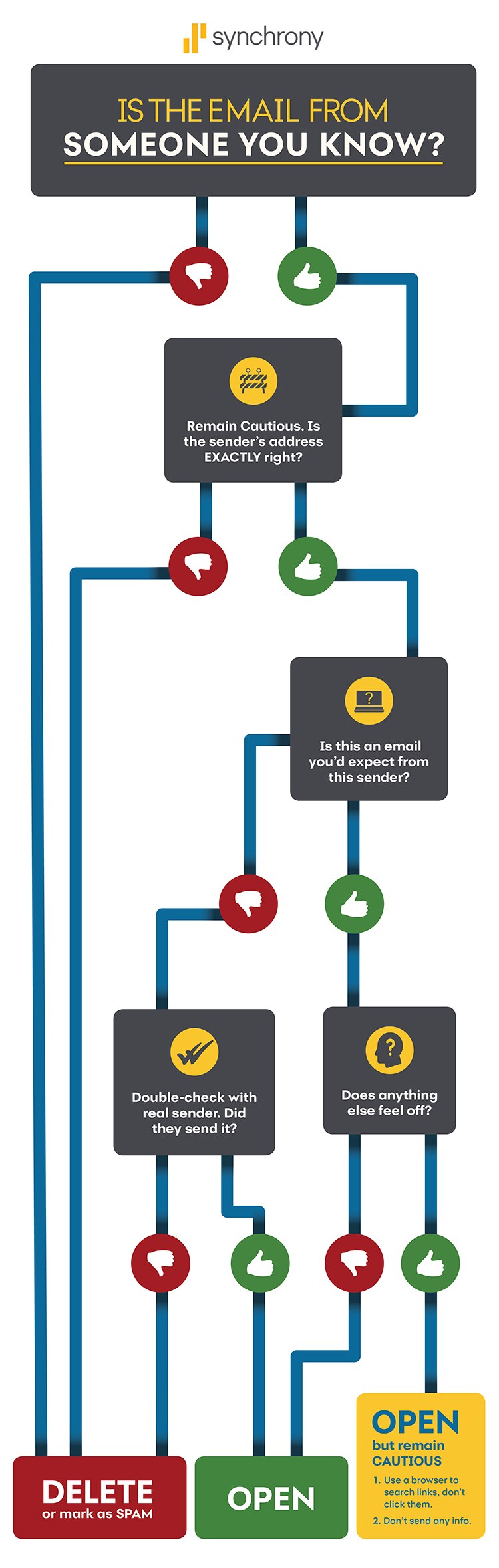
This chart is a decision tree that helps you decide if you should open a suspicious email. The title and first question is "Is this email from someone you know?" If it's not, you should delete it or mark it as spam. If it is, you should remain cautious and ask yourself if the email address is "EXACTLY right". If it isn't, delete it or mark it as spam. If it is, ask yourself if the email is something you'd expect from the sender. If not, double check with the sender and delete it if they say they didn't send it or open it if they say they did. If you would expect this email from the sender, just double check that nothing else feels off before opening it. If you are still concerned, open the email but remain cautious by: 1. Use a browser to search links, don't click on them, and 2. Don't send any info.
Elizabeth Whalen is a freelance writer based in Berkeley, CA. She loves writing about business, financial services and sustainability.
Learn more about keeping yourself safe while banking online.